- DL manuals
- Conceptronic
- Switch
- CB100S24S
- User Manual
Conceptronic CB100S24S User Manual
Summary of CB100S24S
Page 1
©copyright 2008. All rights reserved. Conceptronic cb100s24s & cb100s48s user manual.
Page 2: Table of Contents
English ii table of contents preface...............................................................................................................................................Iv intended readers.........................................................................................................
Page 3
English iii port mirroring ...................................................................................................................................... 25 tftp services ............................................................................................................................
Page 4: Preface
English iv preface the cb100s24s/cb100s48s user manual is divided into sections that describe the system installation and operating instructions with examples. Section 1: introduction describes the switch and its features. Section 2: installation helps you get started with the basic installation of ...
Page 5: Intended Readers
English v intended readers the cb100s24s/cb100s48s user manual contains information for setup and management of the switch. The term, “the switch” will be used when referring to both switches. This manual is intended for network managers familiar with network management concepts and terminology. Typ...
Page 6: Safety Instructions
English vi safety instructions use the following safety guidelines to ensure your own personal safety and to help protect your system from potential damage. Throughout this document, the caution icon ( ) is used to indicate cautions and precautions that you need to review and follow. Safety cautions...
Page 7
English vii • when connecting or disconnecting power to hot-pluggable power supplies, if offered with your system, observe the following guidelines: • install the power supply before connecting the power cable to the power supply. • unplug the power cable before removing the power supply. • if the s...
Page 8
English viii protecting against electrostatic discharge static electricity can harm delicate components inside your system. To prevent static damage, discharge static electricity from your body before you touch any of the electronic components, such as the microprocessor. You can do so by periodical...
Page 9: Section 1
English 1 section 1 introduction • cb100s24s/ cb100s48s switch description • features • ports • front-panel components • side panel description • rear panel description cb100s24s/cb100s48s these switches provide unsurpassed performance, fault tolerance, scalable flexibility, robust security, standar...
Page 10: Ports
English 2 ports the following table lists the relative ports that are present within each switch as well as the features and compatibility for each port type present in the cb100s24s and cb100s48s: cb100s24s description twenty-four 10/100base-t compliant to following standards, ieee 802.3 compliance...
Page 11
English 3 cb100s48s description forty-eight 10/100base-t compliant to following standards, ieee 802.3 compliance ieee 802.3u compliance support half/full-duplex operations all ports support auto mdi-x/mdi-ii cross over ieee 802.3x flow control support for full-duplex mode, back pressure when half-du...
Page 12: Front-Panel Components
English 4 front-panel components cb100s24s • twenty-four 10/100mbps base-t ports • two combo 1000base-t/sfp ports located to the right • two 1000base-t ports located to the right • one female dce rs-232 db-9 console port • leds for power, console, link/act/speed for each port figure 1- 1. Front pane...
Page 13: Leds
English 5 leds the following table lists the leds along with their corresponding description: location led indicative color status description solid light power on power green light off power off solid light console on blinking post is in progress/ post is failure. Per device console green light off...
Page 14: Installing The Sfp Ports
English 6 installing the sfp ports these switches are equipped with sfp (small form factor portable) ports, which are to be used with fiber-optical transceiver cabling in order to uplink various other networking devices for a gigabit link that may span great distances. These sfp ports support full-d...
Page 15: Section 2
English 7 section 2 installation • package contents • before you connect to the network • installing the switch without the rack • rack installation • power on package contents open the shipping carton of the switch and carefully unpack its contents. The carton should contain the following items: • ...
Page 16
English 8 installing the switch without the rack when installing the switch on a desktop or shelf, the rubber feet included with the switch should first be attached. Attach these cushioning feet on the bottom at each corner of the device. Allow enough ventilation space between the switch and any oth...
Page 17
English 9 mounting the switch in a standard 19" rack caution: installing systems in a rack without the front and side stabilizers installed could cause the rack to tip over, potentially resulting in bodily injury under certain circumstances. Therefore, always install the stabilizers before installin...
Page 18: Section 3
English 10 section 3 connecting the switch • switch to end node • switch to hub or switch • connecting to network backbone or server note: all 10/100/1000mbps nway ethernet ports can support both mdi-ii and mdi-x connections. Switch to end node end nodes include pcs outfitted with a 10, 100 or 1000 ...
Page 19: Switch to Hub Or Switch
English 11 switch to hub or switch these connections can be accomplished in a number of ways using a normal cable. • a 10base-t hub or switch can be connected to the switch via a twisted-pair category 3, 4 or 5 utp/stp cable. • a 100base-tx hub or switch can be connected to the switch via a twisted-...
Page 20: Section 4
English 12 section 4 introduction to switch management • management options • web-based management interface • managing user accounts • command line console interface through the serial port • connecting the console port (rs-232 dce) • first time connecting to the switch • password protection • ip a...
Page 21
English 13 9. After you have correctly set up the terminal, plug the power cable into the power receptacle on the back of the switch. The boot sequence appears in the terminal. 10. After the boot sequence completes, the console login screen displays. 11. If you have not logged into the command line ...
Page 22
English 14 first time connecting to the switch the switch supports user-based security that can allow you to prevent unauthorized users from accessing the switch or changing its settings. This section tells how to log onto the switch. Note: the passwords used to access the switch are case-sensitive;...
Page 23: Section 5
English 15 section 5 web-based switch configuration • introduction • login to web manager • web-based user interface • basic setup • reboot • basic switch setup • network management • switch utilities • network monitoring • igmp snooping status introduction all software functions of the switch can b...
Page 24: Web-Based User Interface
English 16 web-based user interface the user interface provides access to various switch configuration and management windows, allows you to view performance statistics, and permits you to graphically monitor the system status. Areas of the user interface the figure below shows the user interface. T...
Page 25: Web Pages
English 17 notice: any changes made to the switch configuration during the current session must be saved in the save changes web menu (explained below). Web pages when you connect to the management mode of the switch with a web browser, a login window is displayed. Enter a user name and password to ...
Page 26: Section 6
English 18 section 6 administration • ip address • port configuration • user accounts • port mirroring • tftp services • multiple image services • forwarding & filtering device information thiswindow contains the main settings for all major functions for the switch and appears automatically when you...
Page 27: Ip Address
English 19 igmp snooping to enable system-wide igmp snooping capability select enabled. Igmp snooping is disabled by default. Enabling igmp snooping allows you to specify use of a multicast router only (see below). To configure igmp snooping for individual vlans, use the igmp snooping window located...
Page 28: Port Configuration
English 20 note: the switch's factory default ip address is 192.168.0.200 with a subnet mask of 255.255.255.0 and a default gateway of 192.168.0.1. To use the bootp or dhcp protocols to assign the switch an ip address, subnet mask, and default gateway address: use the get ip from pull-down menu to c...
Page 29: Port Settings
English 21 port settings click administration > port configuration > port settings to display the following window: to configure switch ports: 1. Choose the port or sequential range of ports using the from…to… port pull-down menus. Use the remaining pull-down menus to configure the parameters descri...
Page 30: Port Description
English 22 the following parameters can be configured: parameter description from…. To use the pull-down menus to select the port or range of ports to be configured. State toggle this field to either enable or disable a given port or group of ports. Speed/duplex toggle the speed/duplex field to eith...
Page 31
English 23 figure 6- 4. Port description window.
Page 32: User Accounts
English 24 user accounts use the user account management window to control user privileges. To view existing user accounts, open the administration folder and click on the user accounts link. This will open the user account management window, as shown below. Figure 6- 5. User accounts window to add ...
Page 33: Port Mirroring
English 25 port mirroring the switch allows you to copy frames transmitted and received on a port and redirect the copies to another port. You can attach a monitoring device to the mirrored port, such as a sniffer or an rmon probe, to view details about the packets passing through the first port. Th...
Page 34: Tftp Services
English 26 tftp services trivial file transfer protocol (tftp) services allow the switch's firmware to be upgraded by transferring a new firmware file from a tftp server to the switch. A configuration file can also be loaded into the switch from a tftp server. Switch settings can be saved to the tft...
Page 35: Multiple Image Services
English 27 multiple image services to configure the files located on the flash memory, use the following windows to guide you. Firmware information thiswindowis used to view boot up firmware images. Figure 6- 10. Firmware information window config firmware image the following window is used to deter...
Page 36: Multicast Forwarding
English 28 to add or edit an entry, define the following parameters and then click add/modify: parameter description vid the vlan id number of the vlan on which the above unicast mac address resides. Mac address the mac address to which packets will be statically forwarded. This must be a unicast ma...
Page 37: Multicast Filtering Mode
English 29 the following parameters can be set: parameter description vid the vlan id of the vlan to which the corresponding mac address belongs. Multicast mac address the mac address of the static source of multicast packets. This must be a multicast mac address. Port settings allows the selection ...
Page 38: Section 7
English 30 section 7 l2 features • vlan • trunking • igmp snooping • spanning tree vlans a virtual local area network (vlan) is a network topology configured according to a logical scheme rather than the physical layout. Vlans can be used to combine any collection of lan segments into an autonomous ...
Page 39
English 31 vlans to span multiple 802.1q-compliant switches through a single physical connection and allows spanning tree to be enabled on all ports and work normally. The ieee 802.1q standard restricts the forwarding of untagged packets to the vlan of which the receiving port is a member. The main ...
Page 40
English 32 figure 7- 2. Ieee 802.1q tag the ethertype and vlan id are inserted after the mac source address, but before the original ethertype/length or logical link control. Because the packet is now a bit longer than it was originally, the cyclic redundancy check (crc) must be recalculated. Figure...
Page 41
English 33 dropped. If the destination port is a member of the 802.1q vlan, the packet is forwarded and the destination port transmits it to its attached network segment. If the packet is not tagged with vlan information, the ingress port will tag the packet with its own pvid as a vid (if the port i...
Page 42: Static Vlan Entry
English 34 static vlan entry in the l2 features folder, open the vlan folder and click the static vlan entry link to open the following window: figure 7- 4. Static vlans entry settings window the 802.1q static vlans window lists all previously configured vlans by vlan id and vlan name. To delete an ...
Page 43
English 35 figure 7- 6. 802.1q static vlans window - modify the following fields can then be set in either the add or modify 802.1q static vlans windows: parameter description vid allows the entry of a vlan id in the add dialog box, or displays the vlan id of an existing vlan in the modify dialog bo...
Page 44: Trunking
English 36 trunking port trunk groups are used to combine a number of ports together to make a single high-bandwidth data pipeline. The switch supports up to six port trunk groups with 2 to 8 ports in each group. A potential bit rate of 800 mbps can be achieved. Figure 7- 7. Example of port trunk gr...
Page 45: Link Aggregation
English 37 load balancing is automatically applied to the ports in the aggregated group, and a link failure within the group causes the network traffic to be directed to the remaining links in the group. The spanning tree protocol will treat a link aggregation group as a single link, on the switch l...
Page 46: Igmp Snooping
English 38 igmp snooping internet group management protocol (igmp) snooping allows the switch to recognize igmp queries and reports sent between network stations or devices and an igmp host. When enabled for igmp snooping, the switch can open or close a port to a specific device based on igmp messag...
Page 47
English 39 the following parameters may be viewed or modified: parameter description vlan id this is the vlan id that, along with the vlan name, identifies the vlan for which to modify the igmp snooping settings. Vlan name this is the vlan name that, along with the vlan id, identifies the vlan for w...
Page 48: Static Router Ports Settings
English 40 static router ports settings a static router port is a port that has a multicast router attached to it. Generally, this router would have a connection to a wan or to the internet. Establishing a router port will allow multicast packets coming from the router to be propagated through the n...
Page 49: Spanning Tree
English 41 click apply to implement the new settings, click the show all static router port entries link to return to the current static router port entries window. Spanning tree 802.1w rapid spanning tree the switch implements the rapid spanning tree protocol (rstp) as defined by the ieee 802.1w sp...
Page 50
English 42 p2p port a p2p port is also capable of rapid transition. P2p ports may be used to connect to other bridges. Under rstp, all ports operating in full-duplex mode are considered to be p2p ports, unless manually overridden through configuration. 802.1d and 802.1w compatibility rstp can intero...
Page 51: Stp Bridge Global Settings
English 43 stp bridge global settings to open the following window, open spanning tree in the l2 features folder and click the stp bridge global settings link. Figure 7- 14. Stp bridge global settings window the following parameters can be set: parameter description spanning tree protocol use the pu...
Page 52
English 44 stp version use the pull-down menu to choose the desired version of stp to be implemented on the switch. There are two choices: stpcompatability - select this parameter to set the spanning tree protocol (stp) globally on the switch. Rstp - select this parameter to set the rapid spanning t...
Page 53: Stp Port Settings
English 45 stp port settings stp can be set up on a port per port basis. To view the following window click l2 features > spanning tree > stp port settings: figure 7- 15. Stp port settings window in addition to setting spanning tree parameters for use on the switch level, the switch allows for the c...
Page 54
English 46 an stp group spanning tree works in the same way as the switch-level spanning tree, but the root bridge concept is replaced with a root port concept. A root port is a port of the group that is elected based on port priority and port cost, to be the connection to the network for the group....
Page 55: Section 8
English 47 section 8 cos • 802.1p default priority • 802.1p user priority the switch supports 802.1p priority queuing quality of service. The following section discusses the implementation of cos (quality of service) and benefits of using 802.1p priority queuing. Understanding ieee 802.1p priority p...
Page 56
English 48 advantages of cos cos is an implementation of the ieee 802.1p standard that allows network administrators a method of reserving bandwidth for important functions that require a large bandwidth or have a high priority, such as voip (voice-over internet protocol), web browsing applications,...
Page 57
English 49 understanding cos the switch has four priority classes of service. These priority classes of service are labeled as 3, the high class to 0, the lowest class. The eight priority tags, specified in ieee 802.1p are mapped to the switch's priority classes of service as follows: • priority 0 i...
Page 58: 802.1P Default Priority
English 50 802.1p default priority the switch allows the assignment of a default 802.1p priority to each port on the switch. In the cos folder, click 802.1p default priority, to view the window shown below. Figure 8- 2. 802.1p default priority window this window allows you to assign a default 802.1p...
Page 59: 802.1P User Priority
English 51 802.1p user priority when using 802.1p priority mechanism, the packet is examined for the presence of a valid 802.1p priority tag. If the tag is present, the packet is assigned to a programmable egress queue based on the value of the tagged priority. The tagged priority can be designated ...
Page 60: Section 9
English 52 section 9 security • 802.1x 802.1x 802.1x port-based and mac-based access control the ieee 802.1x standard is a security measure for authorizing and authenticating users to gain access to various wired or wireless devices on a specified local area network by using a client and server base...
Page 61
English 53 authentication server the authentication server is a remote device that is connected to the same network as the client and authenticator, must be running a radius server program and must be configured properly on the authenticator (switch). Clients connected to a port on the switch must b...
Page 62
English 54 client the client is simply the endstation that wishes to gain access to the lan or switch services. All endstations must be running software that is compliant with the 802.1x protocol. For users running windows xp, that software is included within the operating system. All other users ar...
Page 63
English 55 understanding 802.1x port-based and mac-based network access control the original intent behind the development of 802.1x was to leverage the characteristics of point-to-point in lans. As any single lan segment in such infrastructures has no more than two devices attached to it, one of wh...
Page 64
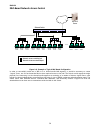
English 56 mac-based network access control 802.1x client network access controlled port network access uncontrolled port radius server ethernet switch 802.1x client 802.1x client 802.1x client 802.1x client 802.1x client 802.1x client 802.1x client 802.1x client 802.1x client 802.1x client 802.1x c...
Page 65
English 57 802.1x authenticator settings to configure the 802.1x authenticator settings, click security > 802.1x > 802.1x authenticator settings: figure 9- 9. 802.1x authenticator settings window.
Page 66
English 58 to configure the settings by port, click on its corresponding ports link, which will display the following table to configure: figure 9- 10. 802.1x authenticator settings window (modify) this window allows users to set the following features: parameter description from/to] enter the port ...
Page 67
English 59 quietperiod this allows you to set the number of seconds that the switch remains in the “held” state following a failed authentication exchange with the client. The default setting is 60 seconds. Supptimeout this value determines timeout conditions in the exchanges between the authenticat...
Page 68: Local Users
English 60 local users in the security folder, open the 802.1x folder and click 802.1x user to open the 802.1x user window. This window will allow the user to set different local users on the switch. Figure 9- 11. Local users configuration window enter a user name, password and confirmation of that ...
Page 69: 802.1X Capability Settings
English 61 802.1x capability settings in the security folder, open the 802.1x folder and click 802.1x capability settings to open the 802.1x capability settings window. This window will allow the user to set capability settings for each port on the switch. Figure 9- 12. 802.1x capability settings wi...
Page 70
English 62 this window displays the following information: parameter description from and to select the port or range of ports to be set. Capability this allows the 802.1x authenticator settings to be applied on a per-port basis. Select authenticator to apply the settings to the port. When the setti...
Page 71: Radius Server
English 63 radius server the radius feature of the switch allows you to facilitate centralized user administration as well as providing protection against a sniffing, active hacker. The web manager offers three windows. Click security > 802.1x > radius server to open the radius server window shown b...
Page 72: Section 10
English 64 section 10 monitoring • mac address • igmp snooping group • browse router port • port access control mac address this allows the switch's dynamic mac address forwarding table to be viewed. When the switch learns an association between a mac address and a port number, it makes an entry int...
Page 73
English 65 the following fields can be viewed or set: parameter description vlan name enter a vlan name by which to browse the forwarding table. Mac address enter a mac address by which to browse the forwarding table. Port select the port by using the corresponding pull-down menu. Find allows the us...
Page 74: Igmp Snooping Group
English 66 igmp snooping group this window allows the switch’s igmp snooping group table to be viewed. Igmp snooping allows the switch to read the multicast group ip address and the corresponding mac address from igmp packets that pass through the switch. The number of igmp reports that were snooped...
Page 75: Browse Router Port
English 67 browse router port this displays which of the switch’s ports are currently configured as router ports. A router port configured by a user (using the web-based management interfaces) is displayed as a static router port, designated by s. A router port that is dynamically configured by the ...
Page 76
English 68 the following fields can be viewed: parameter description serverindex the identification number assigned to each radius authentication server that the client shares a secret with. Serveripaddr the identification ip address of the server. Udp port the udp port the client is using to send r...
Page 77: Auth State
English 69 auth state auth state is unable to be viewed unless the switch is set to port-based or mac-based for the 802.1x function. This table displays the authenticator state for each port. To view the authenticator state, click monitoring > port access control > auth state. Figure 10- 5. Authenti...
Page 78: Reset
English 70 reset the reset function has several options when resetting the switch. Some of the current configuration parameters can be retained while resetting all other configuration parameters to their factory defaults. Figure 10- 6. Traffic. Reset window note: only the reset system option will en...
Page 79: Reboot System
English 71 reboot system the following window is used to restart the switch. Figure 10- 7. Reboot system window clicking the yes radio button will instruct the switch to save the current configuration to non-volatile ram before restarting the switch. Clicking the no radio button instructs the switch...
Page 80: Logout
English 72 logout click the logout button on the logout window to immediately exit the switch. Figure 10- 9. Logout window.
Page 81: Appendix A
English 73 appendix a technical specifications general protocols fiber-optic ieee 802.3 10base-t ethernet ieee 802.3u 100base-tx fast ethernet ieee 802.3ab 1000base-t gigabit ethernet ieee 802.3z 1000base-t (sfp “mini gbic”) ieee 802.1d spanning tree ieee 802.1d/s/w spanning tree ieee 802.1q vlan ie...
Page 82
English 74 physical and environmental internal power supply 40w ac input 100-240vac, 12v/3.33a , 50~60hz operating temperature 0 - 40°c storage temperature -40 - 70°c humidity 5 - 95% non-condensing dimensions 19” metal case 441(w) x 207(d) x 44(h) mm, 1u rack-mount size (cb100s24s) 441(w) x 309(d) ...
Page 83
English 75 power feature detailed description internal power supply 40w ac input 100-240vac, 12v/3.33a , 50~60hz performance feature detailed description wire speed on all fe/ge ports full-wire speed (full-duplex) operation on all fe/ge ports forwarding mode store and forward switching capacity 12.8...
Page 84
English 76 port functions feature detailed description console port dce rs-232 db-9 for loading factory reset purpose 24 x 10/100baset ports 48 x 10/100baset ports compliant to following standards, 1. Ieee 802.3 compliance 2. Ieee 802.3u compliance 3. Support half/full-duplex operations 4. All ports...
Page 85: Appendix B
English 77 appendix b system log entries the following table lists all possible entries and their corresponding meanings that will appear in the system log of this switch. Category event description log content severity system system started up uint , system started up critical configuration saved t...
Page 86
English 78 category event description log content severity port link down port link down informational console successful login through console unit , successful login through console (username: ) informational login failed through console unit , login failed through console (username: ) warning log...
Page 87
English 79 category event description log content severity snmp snmp request received with invalid community string snmp request received from with invalid community string! Informational stp topology changed topology changed informational new root selected new root selected informational bpdu loop ...
Page 88
English 80 category event description log content severity login failed through web authenticated by aaa local method login failed failed through web from authenticated by aaa local method (username: , mac: ) warning successful login through web(ssl) authenticated by aaa local method successful logi...
Page 89
English 81 category event description log content severity successful login through telnet authenticated by aaa none method successful login through telnet from authenticated by aaa none method (username: , mac: ) informational successful login through ssh authenticated by aaa none method successful...
Page 90
English 82 category event description log content severity successful enable admin through console authenticated by aaa local_enable method successful enable admin through console authenticated by aaa local_enable method (username: ) informational enable admin failed through console authenticated by...
Page 91
English 83 category event description log content severity successful enable admin through ssh authenticated by aaa none method successful enable admin through ssh from authenticated by aaa none method (username: , mac: ) informational successful enable admin through console authenticated by aaa ser...
Page 92
English 84 category event description log content severity safeguard engine is in filtering packet mode safeguard engine enters exhausted mode warning packet storm broadcast strom occurrence port broadcast storm is occurring warning broadcast storm cleared port broadcast storm has cleared informatio...
Page 93: Appendix C
English 85 appendix c cable lengths use the following table to as a guide for the maximum cable lengths. Standard media type maximum distance mini-gbic 1000base-lx, single-mode fiber module 1000base-sx, multi-mode fiber module 1000base-lhx, single-mode fiber module 1000base-zx, single-mode fiber mod...
Page 94: Appendix D
Appendix d glossary 1000base-sx: a short laser wavelength on multimode fiber optic cable for a maximum length of 2000 meters 1000base-lx: a long wavelength for a "long haul" fiber optic cable for a maximum length of 10 kilometers 100base-fx: 100mbps ethernet implementation over fiber. 100base-tx: 10...
Page 95
Fast ethernet: 100mbps technology based on the ethernet/cmsa/cd network access method. Flow control: (ieee 802.3z) a means of holding packets back at the transmit port of the connected end station. Prevents packet loss at a congested switch port. Forwarding: the process of sending a packet toward it...
Page 96
Server farm: a cluster of servers in a centralized location serving a large user population. Slip: serial line internet protocol: a protocol, which allows ip to run over a serial line connection. Snmp: simple network management protocol: a protocol originally designed to be used in managing tcp/ip i...